![]() Security Testing and Validation Services
Security Testing and Validation Services
Find and fix gaps in your IT and security architecture

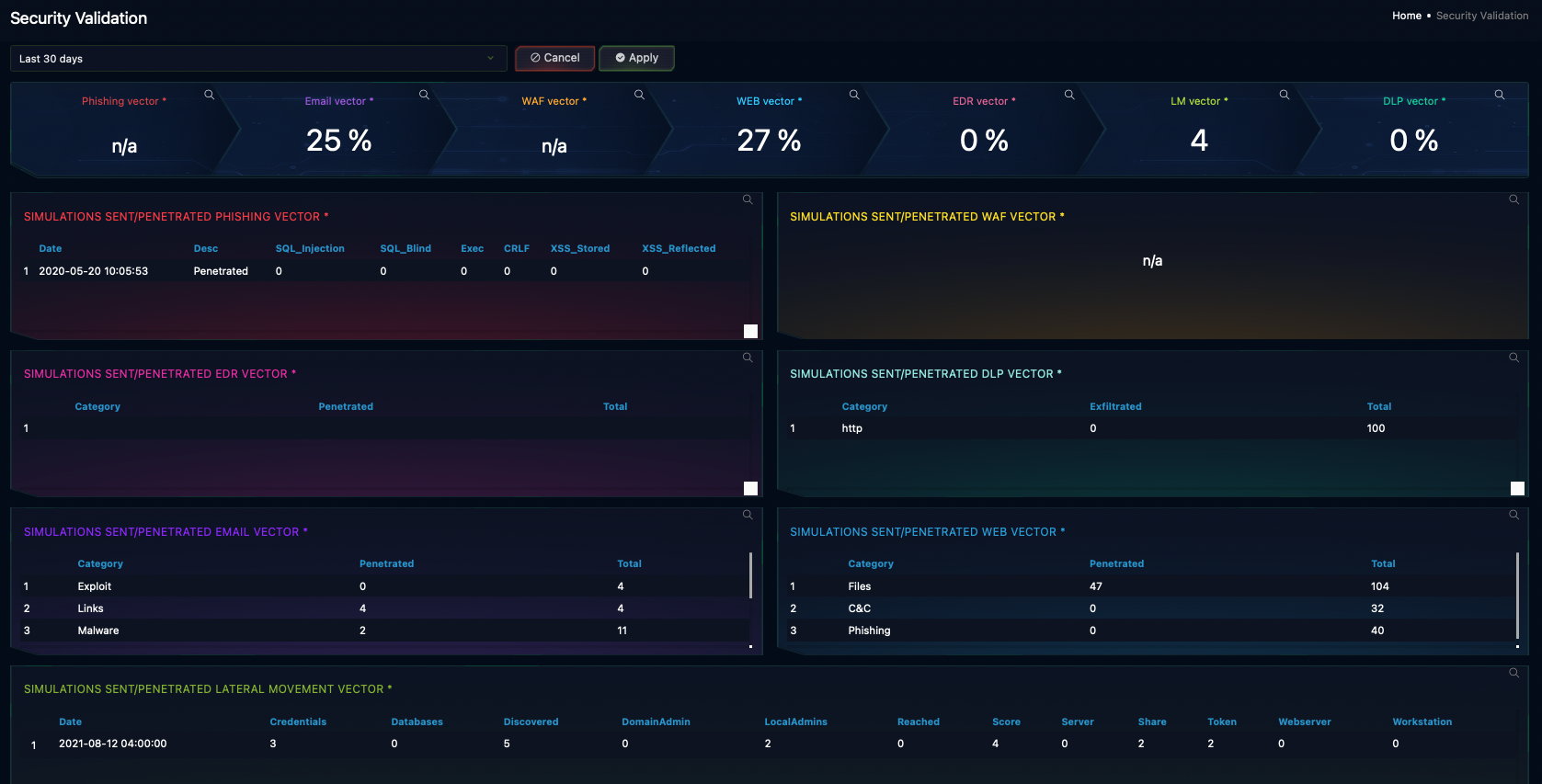
Click image for more detail.
Proactively uncover and close weaknesses in your IT and security controls to reduce cyber risk and boost resilience to attacks. GLESEC provides comprehensive security assessments, pentests, and managed breach and attack simulations to ensure your architecture, applications, data, assets, and people remain safe and your organization meets regulatory and compliance requirements.
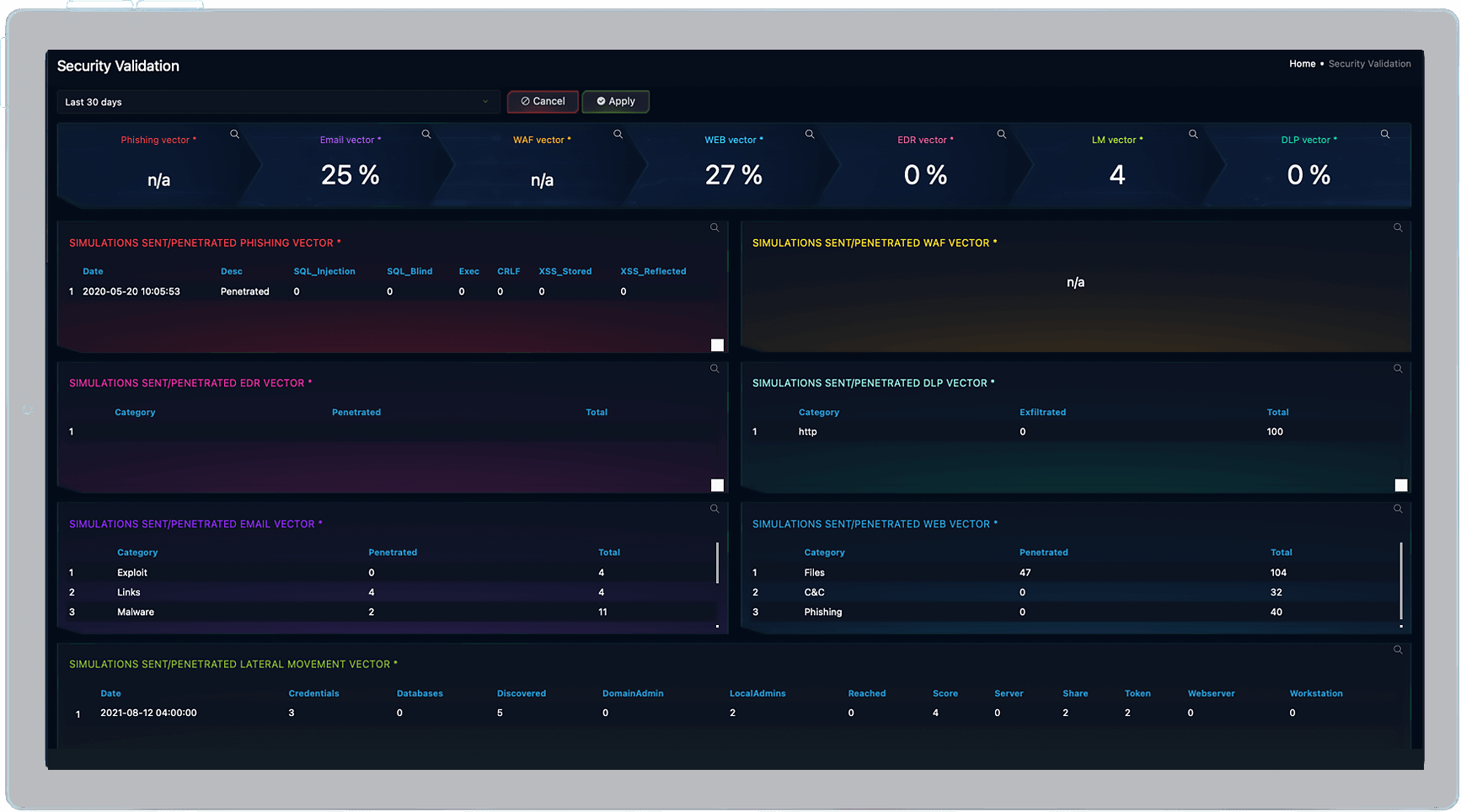
Click image for more detail.
![]() There’s More To Security Testing Than Pentests
There’s More To Security Testing Than Pentests

PROBLEM
Misconfigurations and wrong tools cause breaches
Many organizations unknowingly have vulnerabilities in their security posture and IT architecture caused by poorly chosen or configured security controls. This creates a false sense of security that is only dispelled when a serious breach occurs.

SOLUTION
Rigorous testing is the only way to uncover security gaps
GLESEC provides an intelligent combination of security testing and validation of security controls to proactively uncover and resolve gaps before an attacker can exploit them.

IMPACT
Tighten your cybersecurity posture
Proactively boost cyber resilience and build a realistic understanding of your organization’s cyber risk profile by systematically finding and closing vulnerabilities and security gaps.
![]() FAQs
FAQs
FAQ's

You ask, we answer!
Most MSSPs provide simple tools, sometimes with a basic management service. At GLESEC, we don’t believe this is enough to protect your organization against the ever-growing range of cyber threats.
We provide an intelligent combination of technology, management, and professional services tailored to your specific needs and infrastructure. Our services deliver the most comprehensive protection available anywhere—at a much lower cost than building in-house.
Most organizations have too many tools but lack the time and skills to properly configure or manage them. This results in a false sense of security, while still consuming precious time and resources.
GLESEC combines leading technologies with comprehensive managed and professional services to address your real business needs: easier compliance, accurate risk management, and greater resilience to cyberattacks.
We can do almost everything on your behalf - including responding to security incidents - based on pre-agreed rules of engagement. In a few cases, such as patching vulnerabilities in IT infrastructure, we provide full guidance and support to help your in-house team take the necessary steps.
For organizations with established incident response capabilities, we adapt our services to best support your existing personnel and workflows.
No. In most cases, it’s more cost effective to outsource cybersecurity to a trusted provider. Remember—it’s not just the cost of a tool to consider, it’s the total cost of configuring, managing, and maintaining that tool over it’s lifetime and replacing it next time you refresh your stack.
Here’s an example. A customer of ours once bought a tool instead of opting for our manage service equivalent. While the tool seemed cheap initially, the customer needed three staff to manage, maintain, and utilize it, making the tool a lot more expensive than our managed service.
![]() TECHNOLOGY PARTNERS
TECHNOLOGY PARTNERS
TOOLS BY THEMSELVES
ARE NOT ENOUGH TO FIND AND FIX GAPS IN YOUR IT AND SECURITY ARCHITECTURE
Validate
Your IT and Cybersecurity Posture
Find out how GLESEC can help you uncover weaknesses and validate your cybersecurity controls.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.